ORIE 480 Study Sheet Midterm
Transcript of ORIE 480 Study Sheet Midterm
-
8/14/2019 ORIE 480 Study Sheet Midterm
1/9
ORIE 480 Study Sheet: MIDTERMJames YuJane Thipphavong
Lecture 1: Database Systems Intro Data: Raw facts that are described, observed, or measured
Information: Data that has been organized or prepared
Knowledge: Data/Information/Rules that are used for actual decision making
Database Management System (DBMS): A collection of programs that
define/manipulate/maintain databases
Database: A collection of interrelated data
File Systems are unattractive
o Data-program dependence: must write custom programs to query
o Redundancy
o Inconsistency
o Lack of securityo Have to write your own
o If a query has not been foreseen, an expert programmer is needed
Different types of DBMS
o Hierarchical
o Network
o Relational
o Object-oriented
Database Tables Restrictions
o Columns contain same type of data
o One value per cell
o One (or more) column(s) contains a unique value for each row
Primary Keyo Rows have the same size (# of columns)
Order is unimportant, and are dynamic
Transactions
o Logical unit of access to a DBMS
o Concurrency and Recovery from system crashes
o Locks, Write-Ahead Logs and Checkpoints
2 Components of RDBMS
o Data Definition Language (DDL)
Allows you to define metadatao Data Manipulation Language (DML)
Allows you to insert/edit/delete/ask questions about data
QBE, SQL
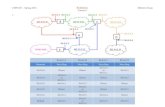
Lecture 2: Designing Databases Entity-Relationship Diagrams Entities: things about which one wants to store info
Attributes: the info one wants to store about the entity
Relationships: Associations between two or more entities
Cardinality: 1:1, 1:N, N:M
-
8/14/2019 ORIE 480 Study Sheet Midterm
2/9
Participation
o Total Participation: every student must have an advisor
o Partial Participation: a professor may not be teaching any classes
o Circle: Denotes partial participation for the opposing box (think race relations
and throwing the balls)
o Referential Integrity:A database entry should refer to something that exists
Weak Entity: Part of its key is in another entity
Primary Key: An attribute that uniquely determines a record
Foreign key: An attribute in one entity which is the primary key of another entity to which
the table is related
Mapping ERDs to Tables
o 1:1
Put the primary key of 1 entity to the table of the other 1 entityo 1:N
Put the primary key of 1 entity to the table of the N entityo N:M
Create new table consisting of primary keys of both tables
Lecture 3: WWW Client Server Model
o Client opens a connection, makes a request
o Server returns file
o Connection closed
WWW runs on HyperText Transfer Protocol
o GET requests an item
o HEAD requests information about an item (then check if stored in cache)
Many IT systems and definitely the WWW are too large for a person to use effectively, so
develop searching tools
Lecture 4: Query by Example and SQL Done by Examples
Lecture 5: Internet Markup Languages and Regular Expressions HTML
o Very simple
o Fail-soft principle: If your tags are wrong, something still appears
o Apply formatting tags to basic elements
o Meta tags provide information
o Structural versus formatting tags
SGML
o
Standard generalized markup languageo What HTML is based on, pre-defined tags
XML
o eXtensible Markup Language fordescribinginformation
o user-defined tags
o extensibility
o precise structure
o valid Document Type Definition (DTD)
DTD is a grammar for the XML document
-
8/14/2019 ORIE 480 Study Sheet Midterm
3/9
o eXtensible Stylesheet Language (XSL)
o XML is becoming the standard front end of databases on the Web
o DBMS are incorporating XML output capabilities
Lecture 6 and 7: Networkso Circuit Switched: end systems are connected to senders by an end-to-end reserved
circuit.
o Datagram Networks: Every packet has full addressing information, and can be routed
independently of others.
o Layers of Networks: Host -> TCP or UDP -> IP -> Subnetwork -> Physical Media
o An identifier for a computer or device on a TCP/IP network. Networks using the TCP/IP
protocol route messages based on the IP address of the destination. The format of an IPaddress is a 32-bit numeric address written as four numbers separated by periods. Eachnumber can be zero to 255. For example, 1.160.10.240 could be an IP address.
o UDP: User Datagram Protocol,
o Demuxing layer
o In order to know which process to send the packet to (email, ftp, ,telnet, web, etc)
o TCP (Transmission Control Protocol)
o Packet Sequencingo Flow control
o Domain Name System (DNS): distributed Internet directory service. DNS is used mostly
to translate between domain names and IP addresses, and to control Internet emaildelivery. Most Internet services rely on DNS to work, and if DNS fails, web sites cannotbe located and email delivery stalls.
o Email: Client sends to Sendmail server, which sends to Mail Transfer Agent (MTA), which
queries the DNS and sends to the destination MTA, which sends to the destinationGetmail server, and finally to the receiving client.
o Firewalls
o Kind of router
o Prevents unwanted packets from entering a site
o
Hackers could still hack into the mail server and gain access to siteo DMZ (Demilitarized Zones) evolved let mail server reside outside firewall to
prevent hackers from gaining access to site through mail server (and other suchservers)
o IP Address Distribution Problem
o Improve the efficiency of address assignment
o Design a new IP with more address space
o Dynamic IP address assignment
o Network Address Translation; Gives hosts non-global addresses and translates
them to global addresses on the flyo Virtual Private Network (VPN)
o The concept of including a node in a public network (internet) into a sites private
networko Using tunneling and encryption for security
o Dial-up Roaming
o ISPs having roaming agreements with other ISPs via a common mediator
o Allows you to access your ISP in many different cities around the country
Lecture 8: Dynamic and Active Web Technologieso Static: a file resides on the web server
o Pros: cheap and fast
-
8/14/2019 ORIE 480 Study Sheet Midterm
4/9
o Cons: inflexible, revisions are hard, may need many documents compared to
dynamic
o Dynamic: document is created upon request (by server)
o Pros: flexible; current
o Cons: uses server resources, slower, costly to create and debug; cant display
changing information; security issues for the server
o State Information Information that program saves between invocations
o Active: Server returns a program which runs in users browser
o Pros: flexible
o Cons: Costly and difficult to create and debug; security risk for the client
o Java active documents are called applets
o Javascript: browsers read and interpret javascript embedded in html
Lecture 9: Introduction to Decision Analysis Goal: Make decisions
o Well grounded probability
Probability
o P(A|B) = P(AB) / P(B)
Lecture 10: Decision Analysis Biases Human Limitations on Information Processing
o Short-term memory
o Unreliable recall of information
o Slow numerical calculations
o Inaccuracy from Biases
Two Models of Decision Making
o Fully Rational Approach
Requires complete, perfect, and instantaneous information
Requires solution to hard computational problems
Rationality = Expected utility maximization
o Satisficing (bounded-rational) approach
Use of limited amount of information, heuristics
Heuristics
o Availability Heuristics
What is easily recalled must be most likely
Biases
Ease of recall
Retrievability
o Representativeness Heuristics
Beliefs about what are representative examples of particular groups of
events Biases
Insensitivity to base rates
Misconceptions of chance
o Anchoring and adjustment heuristics
Starting somewhere and adjusting
Biases
Over reliance on initial guess and overconfidence
-
8/14/2019 ORIE 480 Study Sheet Midterm
5/9
Decision Analysis
o Advantages
Models rich problem structure
Well grounded in theory
Formal methods to compute optimal solutions
Avoids human biases
Sensitivity analysis
o Disadvantages
Abstract model: may be to simple
Uncertainty can still exist
Model can include biases
Size and complexity of model can become horrendous
Lecture 11: Decision Trees Maximax: Choose decision that yields maximum profit
Maximin: Choose decision that would make you lose the least amount of money
Regret Matrix: Difference in the amount of profit if you had chosen
Least Regret Decision: Choose decision that generates least amount of regret in any
case
Decision Tree
o Solving a Decision Tree
Compute the posterior conditional probabilities
Ie. P(good market | forecast good)
Compute the values at the outcome nodes
Work back from outcome nodes towards the root node
Read off the optimal decision at teach decision nodeo Advantages
Structures a decision process
Evaluates all possible outcomes
Decision making process is succinct
Focuses decision on financial figures, probability, and assumptions
Sensitivity analysis
Lecture 12: Information Systems in Enterprises Information Architecture Structure
o Hierarchy of Levels
Strategic
Management
Knowledge
Operationalo Departments
Sales and Marketing
Finance
Accounting
Manufacturing
Human Resourceso IT Infrastructure
Hardware
Software
-
8/14/2019 ORIE 480 Study Sheet Midterm
6/9
Data and Storage
Networkso 6 Major types of Information Systems
Executive Support Systems (ESS) (Strategic Level)
Management Information Systems (Management Level)
Decision Support Systems (Management Level)
Knowledge Work Systems (Knowledge Level) Work Stations (Knowledge Level)
Transaction Processing Systems (Operational Level)
OLTP
o A type of computer processing in which the computer responds immediately to
user requests. Each request is considered to be a transaction. Automatic tellermachines for banks are an example of transaction processing.
o ACID test
Atomicity (all or nothing)
Consistency (The database is transformed from one valid state toanother valid state.)
Isolation (The results of a transaction are invisible to other transactions
until the transaction is complete) Durability (Once committed (completed), the results of a transaction are
permanent and survive future system and media failures)
Batch
o The opposite of transaction processing is batch processing, in which a batch of
requests is stored and then executed all at one time. Transaction processingrequires interaction with a user, whereas batch processing can take place withouta user being present.
MIS issues
o Multiple entries of same data
o Multiple versions of the same element
o Conflicting data definitions
o
Nonstandard systems interfaceso Data glut
o Inflexibility
o Report writing backlog
o Data ownership and hoarding
o Lack of timeliness
Business Processes
o Before: Stovepipe Systems
o After: Enterprise System
On Line Analytical Processing
o a key reporting and analysis tool for operations and strategic planning
o Query-driven, usually over multidimensional DB
o most OLTP systems unsuitable for OLAP: OLTP will slow down OLAP
Data Warehouses
o Source of data for OLAP
Includes analytical toolso Key enabler is Metadata
Identifies the technical aspects of the data
Identifies the business meaning of the data
Provides utilization tools
Data Mining
-
8/14/2019 ORIE 480 Study Sheet Midterm
7/9
-
8/14/2019 ORIE 480 Study Sheet Midterm
8/9
Lecture 14: MIS Design and Implementation- Key Components of Systems Analysis
o Decisions
o Transactions and Processing
o Information and its flow
o Individuals and functions involved
o Communications and coordination- Systems life cycle
o Inception
o Systems analysis
o Feasibility Study
o Design
o Specifications
o Building the system
o Testing
o Training
o Conversion & Installation
o Maintenance & Enhancements
-Critical Success Factors
o A small number of objectives on which IS must focus
o Attention on how things should be
- Data Collection for Analysis and Designo Observation
o Interview
o Questionnaires
- Design Methodologieso Structured (e.g. Data flow diagrams)
o Objected Oriented Model (UML: universal modeling language)
- Testing- Conversion
o Parallel Strategy: run both old and new system
o Direct cutover: kill old system and use new oneo Pilot Study: implement new system in one part of company
o Phased Approach: intro system in stages instead of all at once
- Training and Documentation- User-oriented Design
o Use of prototypes
o Prototypes are quickly made and have flexible design
- Outsourcingo Advantages
May pay only what you use
Access to top talent
Frees up company resourceso
Disadvantages Underestimate cost of finding and evaluating vendors
Monitoring
Loss of control- Causes of successes and failures
o Funding
o Insufficient user involvement
o User-Designer communications gap
o Insufficient management support
-
8/14/2019 ORIE 480 Study Sheet Midterm
9/9
o Level of complexity
Project size
Project structure
Experience with technologyo Politics
o Non-systematic approach to changes